VPCSML* Multilevel Authentication System Technical Details
VPCSML is a new authentication system for authorisation that acts independently of client devices to assist the network administrator to better protect user privacy and protect network resources from unauthorised use.
Essentially VPCSML stops people being tricked into inadvertently revealing their network access credentials to a spoofed authentication request more commonly referred to as a credentials phishing attack.
The design is a significant improvement on the original topology that is widely in use that was created by MIT students in the 1960's. Authentication occurs remotely it is not interpreted on the client device as this is a significant weakness of the current authentication topology in use (because they use the ascii or unicode tables which are widely distributed and commonly known and consequently provide poor security).
Instead interpretation occurs on the server using a proprietary matrix as this prevents keylogging malware. This enables the design to be used as a secure means of allowing access to for example networks, bank accounts, cars and buildings etc from a mobile device without the risk of losing control of access.
If the device is lost, broken, stolen or becomes obsolete because the authentication is independent of the device the user is not locked out if they need to use a different device. If the user loses their device they can gain access by simply purchasing another device there is no need to re-register or install authentication apps as the authentication all occurs on the server side.
The multilevel proprietary number system design protects network users from large scale pharming and phishing attacks. Each time the user logs on to a network with VPCSML the server provides a onetime matrix value assigned to each of the keys allocated to the user from which the user selects their credentials. The co-ordinate values of each key depressed are transmitted back to the server one at a time in encrypted format for decoding and assembly and then are interpreted on the server and compared with the stored salted hash value of the client credentials that are stored on the server at the time of user registration.
Each time a keyboard is presented for credentials selection by the user it is resorted (this can be disabled but it is not recommended) this assists with making vector analysis more difficult. Keyboard feed back is disabled to prevent screen capture malware.
User experience is greatly enhanced as there is a simple registration process and easy to remember picture keys. The user is not required to contend with installing any device dependent software or hardware or requirements to choose complex difficult to remember long passwords.
The user is not inconvenienced if their device is lost, stolen, damaged or becomes obsolete as they can simply access the network on a new device without any requirement to re-register this will assist network owners in containing help desk costs and prevents attackers exploiting re-registration procedures to take over user accounts.
The VPCSML routines allow for a combination of timeouts and lockouts. Time outs occur on the upper level with lockouts reserved for lower levels this prevents users from being inconvenienced by hacking attacks, or deliberate attempts to lock users out but still allows for lockouts to prevent brute force attacks and to comply with statutory requirements for lockouts to be applied.
VPCSML provides a unique key set for each and every user on a network from which to select their credentials. This results in the user receiving a custom set of credentials making hacking attacks more difficult as they have to be customised to the individual.
The customised keyboard and credentials provide an easy way for the user to know with confidence that they are logging onto the correct site, which is now becoming more of a dilemma for users with more and more sites accessed being hosted on cloud configurations that may not follow traditional naming conventions and where site references and links are continually changing and expanding.
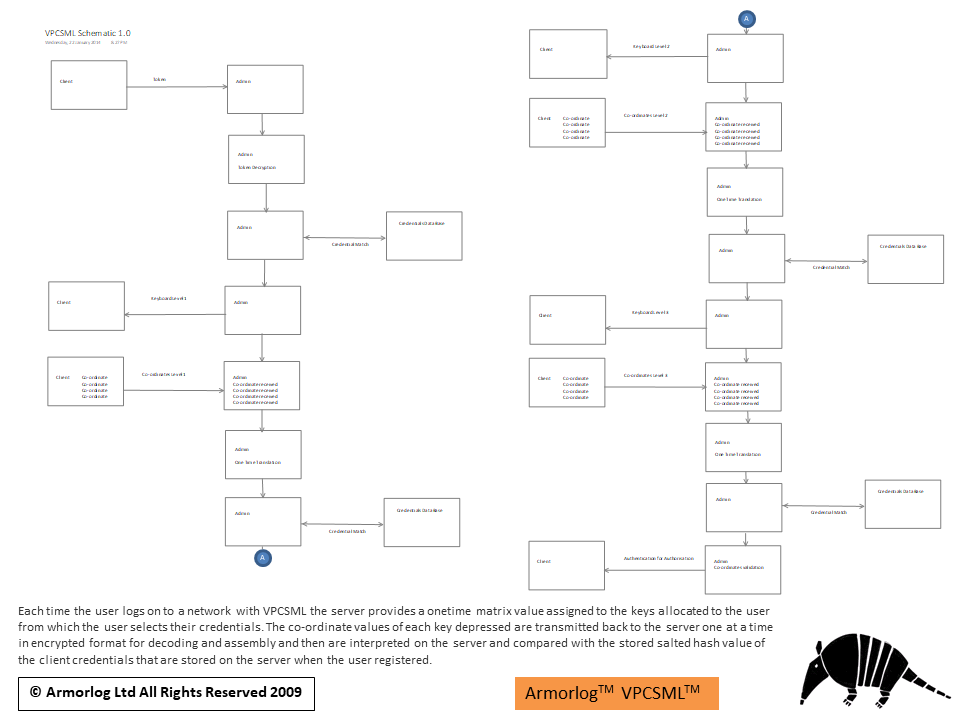
This diagram outlines the VPCSML* onetime matrix co-ordinates input processing.